content management system (CMS)
What is a content management system (CMS)?
A content management system (CMS) is a software application that lets users create, edit, collaborate on, publish and store digital content. CMSes are typically used for enterprise content management (ECM) and web content management (WCM).
How does a CMS work and how is it used?
A CMS provides a graphical user interface with tools to create websites, and to edit and publish web content without the need to write code from scratch.
A CMS has two components: a content management application (CMA) and a content delivery application (CDA).
- The CMA is a graphical user interface that lets users design, create, modify and remove content from a website without the need for Hypertext Markup Language (HTML) knowledge.
- The CDA component provides the back-end services that support management and delivery of the content once a user creates it in the CMA.
What's the difference between CMS, ECM and WCMS?
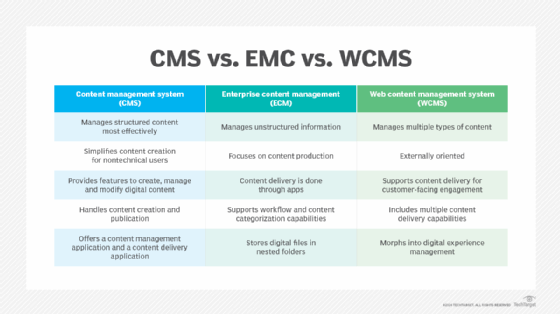
A CMS, ECM system and WCMS all manage content, but there are differences between them:
- The CMS is the precursor to the ECM system. A CMS is a place to create, manage and store digital content. It works best with structured content -- such as documents and database records.
- An ECM system manages both structured and unstructured content. It includes software, strategies and security to effectively manage content.
- A WCMS is like an ECM system, but the WCMS is for web content -- such as product pages on e-commerce websites. A WCMS contains a publishing tool and facilitates collaborative authoring.
CMS features
Features can vary among the various CMS software offerings, but core functions include the following:
- Intuitive indexing, search and retrieval. These features index all data for easy access through search functions and let users search by attributes such as publication dates, keywords or author.
- Format management. This helps turn scanned paper documents and legacy electronic documents into HTML or PDF documents.
- Revision features. These features let users update and edit content after initial publication. Revision control also tracks any changes users make to files.
- Publishing and content creation. This functionality lets individuals use a template or a set of templates that an organization approves -- as well as wizards and other tools -- for content creation and modification.
A CMS can also provide tools for personalization, or one-to-one marketing. One-to-one marketing is the ability of a website to tailor its content and advertising to a user's specific characteristics using information a user provides or a website gathers. For example, if a user searches for digital cameras in major search engines -- such as Google -- advertising banners might feature businesses that sell digital cameras instead of businesses that sell gardening products.
Other CMS features include the following:
- URLs designed to help search engine optimization (SEO-friendly URLs).
- Integrated and online help, including discussion boards.
- Tools for team-based collaboration among content creators and for document management.
- Group-based permission systems and security.
- Workflows for content creator, editor and administrative roles to streamline security and permissions.
- Full template support and customizable templates.
- Easy wizard-based installation and versioning procedures.
- Admin panel with support for multiple languages.
- Minimal server requirements.
- Integrated file managers.
- Integrated audit logs.
Benefits of using a CMS
There are several benefits of using a content management system, including the following:
- Ease of use. A graphical user interface makes it easy for even those with limited technical knowledge to use the software.
- Low cost of entry. Some CMS platforms are free while others charge a monthly fee, but all require little or no high-end IT skills to implement, lowering the cost of website deployment considerably.
- Easy to search for information. A built-in search function lets users enter what they're searching for and returns a list of items -- much like a Google search engine.
- Easy to manage content. Not only is creating content easy, but so is removing content. A CMS makes it easy to unpublish content to keep websites current.
- Accessible from anywhere. A CMS can be cloud-based or on-premises, but users can access content from anywhere with a device that's connected to the internet.
- Allows multiple users. A CMS makes it easy to manage publishing permissions.
- Instant content updates. A CMS lets users manage and update content in real time -- without having to wait for a developer.
- Easy to scale. A CMS makes it easy for organizations to add new web pages as their business grows without the need for a developer.
- Easy to update. Development teams can roll out updates with just a few clicks.
How to choose the best CMS for your website
There's almost no limit to the factors that must be considered before an organization invests in a CMS. There are a few basic functionalities to always look for, such as an easy-to-use editor interface and intelligent search capabilities. However, for some organizations, the software they use depends on more specific requirements.
For example, consider the organization's size and geographic dispersion. The CMS administrator must know how many people will be using the application, whether the CMS will require multilanguage support and what size support team will be needed to maintain operations. It's also important to consider the level of control both administrators and end users will have when using the CMS. Organizations must also consider the diversity of the electronic data forms that they use. All types of digital content should be indexed easily.
The following are some additional guidelines for choosing the right CMS:
- Get input from employees and leadership. It's important to know who will be using this new CMS and what they'll be using it for. Businesses should involve the marketing team, chief content officer, IT staff and others.
- Assess current and future business needs. A CMS must address an organization's current needs and future business plans. Considerations include whether the system will integrate with the business's current tech stack, and whether it incorporates forward-thinking features such as RESTful application programming interfaces.
- Research options. Businesses should create a short list of software that meets their needs and learn about these options -- this includes talking to users with similar use cases to learn about their experiences with the products.
- Write a request for proposal. An RFP gives vendors the opportunity to address an organization's needs and explain why they can provide the right software for the job.
- Evaluate vendor responses. Businesses should consider the functionality, training and support that each vendor offers. Demos help organizations understand how each system works and what integrations it offers.
Examples of different CMSes
There are several free and subscription-based CMSes available for personal and enterprise use. The following are some examples of content management system providers and their offerings:
- Drupal. Designed for large organizations -- including government agencies -- this CMS offers a large library of modules and themes, making it easy to customize and deploy. Drupal can handle large volumes of traffic and is easy to create new roles and permissions.
- Joomla. This free open source web content management system is built on a model-view-controller framework. It's written in PHP (Hypertext Preprocessor) script language and offers features such as caching, RSS feeds, blog posts, search and support for language translation.
- Magento. Crafted for e-commerce sites, Magento offers high scalability and flexibility. Users can create and manage multiple stores in different languages, while coordinating shipping on a global level. Magento from Adobe offers both free and paid plans.
- Squarespace. Squarespace is user-friendly and ideal for bloggers and small businesses that require a creativity-oriented online presence. It includes built-in sales and SEO tools.
- Wix. This cloud-based CMS offers both free and paid plans. Features include team collaboration tools, third-party integrations, enterprise-grade security, hundreds of premade design templates and the ability to add custom code. Wix provides 24/7 customer support.
- WordPress.org. This free open source WCMS is based on PHP and MySQL. Organizations can use WordPress in the cloud or deploy it on a local computer to act as its own web server. This software is highly customizable, with many paid and free themes and WordPress plugins available. It's also a popular blogging platform.
Enterprise video content management uses various technologies, platforms and services to create and distribute videos within an organization. Learn what benefits video applications offer and how to select a video CMS.







