Ultimate guide to team collaboration platforms
This in-depth team collaboration platform guide examines how to create a virtual environment that promotes secure user engagement, productivity and innovation.
Before the COVID-19 pandemic, team collaboration platforms served as a complement to in-person meetings. Once workforces became largely remote, these platforms -- which include chat, messaging, presence, voice calling, video conferencing, file sharing and more -- became a primary hub for an organization's employees and partners to communicate and collaborate. This guide goes in depth on the benefits, challenges, security concerns, buying considerations and best practices for managing team collaboration platforms.
What are team collaboration platforms?
Team collaboration platforms have grown over the years from a simple communications channel to a powerhouse for an organization, enabling task, project and document management. With new capabilities being added all the time, it can be hard to pin down everything these platforms can do.
Here are some core features of team collaboration platforms:
- messaging
- chat
- channels
- voice calling
- video conferencing
- screen sharing
- calendars
- file sharing
Other features can include the following:
- virtual whiteboards;
- application integration with productivity applications, ERP systems or customer service management platforms;
- webinars/training;
- chatbots; and
- AI for more accurate meeting transcripts.
Team collaboration platforms are designed to let users create collaborative virtual workspaces among established and ad hoc teams. Most platforms support privacy and data security policies that protect corporate data and users. They also enable organizations to enforce compliance and regulatory requirements for data sharing and storage, logging, audits/discovery and archiving.
While some team collaboration platforms are available for free, most organizations pay for usage to ensure access to enterprise-level features and security.
The pandemic's impact on team collaboration platforms
At the start of the pandemic, few organizations were fully prepared to work remotely. Yet, seemingly overnight, companies had to deploy an infrastructure that would support integrated, productivity-focused collaboration among their dispersed workforces and keep them connected to partners, suppliers, customers and other members of the business ecosystem.
Platforms such as Cisco Webex, Google Chat, Microsoft Teams and Slack (which Salesforce plans to acquire) became instrumental in meeting this challenge and helping organizations bring virtual collaboration capabilities to a level comparable to in-person collaboration. This was no easy feat for users with varying levels of infrastructure, including compute power, mobility and connectivity. All users needed a seamless, similar and secure experience across geographies and devices.
Find out how the COVID-19 pandemic has affected deployment and usage of team collaboration platforms in this podcast featuring TechTarget Editor at Large Sandra Gittlen and Metrigy Research co-founder Irwin Lazar.
The platforms had to have top-notch integration with other applications -- such as email, calendars and back-end systems -- so application toggling stayed at a minimum. This was a tall order for IT teams trying to find their footing away from their physical offices.
Companies also needed to be in tune with how their employees made use of these platforms as patterns changed quickly. For example, in the early days of the pandemic, users relied heavily on video conferencing but have since experienced "Zoom fatigue" that is making them reduce their video meeting usage. Users also realized if they were going to be permanently remote, they would need features such as virtual whiteboards for better collaboration.
Benefits of team collaboration platforms
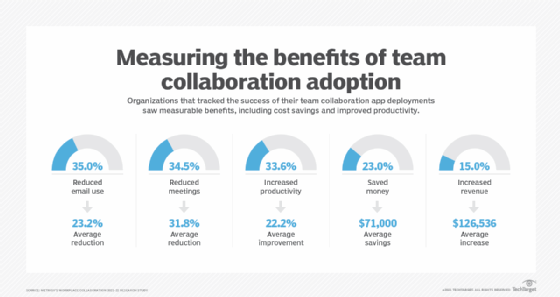
Team collaboration platforms have become a critical business tool because they provide so many benefits for users and organizations alike. Irwin Lazar, co-founder of Metrigy Research, listed some of the business benefits of team collaboration platforms:
- fewer meetings;
- increased productivity;
- cost savings;
- reduction in email; and
- increased revenue, as customer-facing individuals can get answers they need quickly.
Securing team collaboration platforms
As companies settle into a team collaboration environment for their remote workforce, they must review their remote work policies and processes to make sure they align with how users are interacting with the platform.
For instance, if team collaboration platforms started off as an application deployed and managed by different departments, organizations will now want to centralize management with IT and apply single sign-on and other security best practices. Team collaboration platforms should be held to the same standards as other corporate applications and follow regulatory requirements.
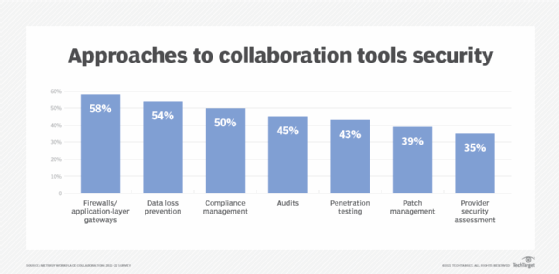
The security concerns associated with team collaboration platforms are the same as with other business applications: phishing, mobile vulnerabilities, compliance and data leaks. These platforms also expose companies to other possible problems, such as toll fraud attacks against their calling infrastructure that can result in financial expense, denial-of-service attacks against networks and on-premises applications, and the potential use of abusive or inappropriate language, which needs to be governed.
One way organizations can lessen their vulnerability is to pare down the number of team collaboration platforms they support in the enterprise, as managing multiple applications can be challenging.
Here are some of the issues presented by using multiple team collaboration platforms:
- application integration;
- understanding risks and enforcing security across numerous platforms;
- deploying and updating features;
- difficulty standardizing user training;
- increased costs;
- greater troubleshooting burden for IT; and
- lack of a consistent user interface.
Cloud-based team collaboration platforms also can pose a risk to organizations and require some basic consideration, including implementing the following cloud collaboration security best practices:
- thoroughly vetting providers, especially any third-party risk;
- weighing how providers handle guest access privileges;
- understanding how providers support layered security controls; and
- developing a user training plan that accounts for the risks of the cloud.
Supporting external collaboration
External collaboration is quickly becoming a must-have in team collaboration platforms as users expect to be able to reach out to people beyond corporate walls and interact the same way they do with their coworkers. Providing such access can be tricky, however.
Guest access and federation are two models that can achieve the goal of external collaboration. Guest access is invitation-based and extends to individual users on a controlled basis, while federation is based on allowing disparate platforms to interwork, as described by Jon Arnold, principal at J Arnold & Associates. While guest access is an easier approach, federation provides far more control, such as limiting the external collaborator's access to certain features. Arnold offered tips for determining the best option for an organization.
Similarly, West Gate President Andrew Froehlich explained how Microsoft, Slack and Cisco each handle federated access, and provided a look at offerings from emerging third-party vendors.
Team collaboration vendors
Team collaboration platforms have so many bells and whistles that figuring out which product is best for an organization might be difficult. Most platforms offer the ability to create persistent channels, rooms or team spaces that enable group communication within the context of a team activity or project and offer one-to-one private chat -- making them a suitable replacement for IM platforms -- according to Metrigy's Lazar.
The differentiators, Lazar said, include the following:
- support for integrated telephony and video meeting features;
- end-to-end encryption, including customer-held encryption keys;
- integration with legacy calling and conferencing platforms;
- off-the-shelf integrations, as well as APIs to enable custom integrations and workflows;
- licensing options and cost; and
- support for cross-company collaboration.
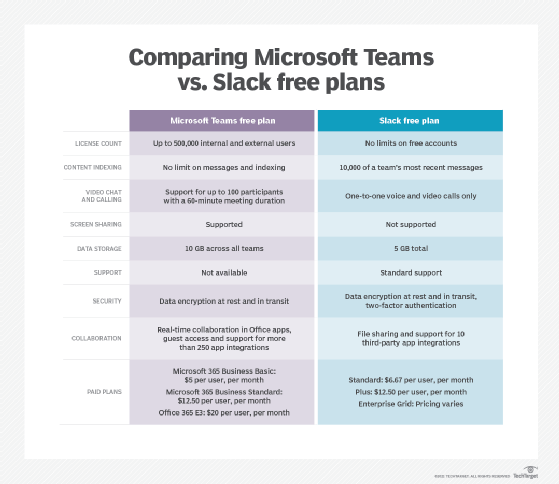
Another worthwhile exercise is to put two of an organization's leading options head-to-head and see how they stack up. For instance, Froehlich did a head-to-head comparison of Microsoft Teams vs. Slack in four key business areas: collaboration basics, video conferencing capabilities, calling and telephony options, and software integrations.
Managing team collaboration platforms
Virtual collaboration is not a deploy-and-done proposition. Leadership and IT teams need to keep adoption and engagement at an optimal level and be ready to make adjustments if they aren't.
The first step is to present the platform as a work hub to employees. Set the expectation that employees must log on to the platform at the start of their day, and make sure all the information they need to plan their day is right there -- project status, meetings, correspondence and tasks, just to name a few. The easier it is for them to stay within the application, the more it will become their central landing place.
Organizations also need to make sure they are deploying the appropriate tools for the work that needs to be done. If a user's job requires video meetings with dozens of participants simultaneously, then a platform with a low maximum number of participants wouldn't fit those needs. Also, be open to users suggesting features, integrations and add-ons that could improve their productivity. Employees will tell you what they need if you listen; something as simple as allowing employees to turn off their cameras during meetings might increase participation because those participants will feel more comfortable.
Encourage employees to engage with one another through channels and other features. Teach them how to use the platform's features. The more empowered they feel, the more likely they are to come up with a productivity or communication improvement that would benefit the whole organization.
Managing team collaboration platforms -- outside of access and security measures -- is oftentimes more about understanding user habits such as workflow and communication preferences. Staying close to users will increase the likelihood of adoption.
The future of team collaboration platforms
Although many organizations are figuring out a fully remote future for their workers and may give up their brick-and-mortar office spaces, others are planning to navigate a hybrid environment. In these scenarios, IT teams will have to figure out how to accommodate mixed participant usage of team collaboration platforms. For instance, if a few participants are in a conference room in the office and others are dispersed in home offices, how does an organization ensure everyone has individual access to chat, screen sharing, whiteboards and other critical features?
Expect team collaboration to get smarter because AI will be embedded deeper into platforms. Along with meeting transcriptions, automation will be applied to meeting invite lists, post-meeting action items, workflow improvements and other collaboration efforts.
Metrigy's Lazar described the future of team collaboration as a core hub where people start their workday that ties together other necessary data sources and applications.







