information governance
What is information governance?
Information governance is a holistic approach to managing corporate information by implementing processes, roles, controls and metrics that treat information as a valuable business asset.
Information governance also includes a defined accountability framework and decision rights specification to ensure the proper creation and use of information, its storage and access. This includes controls on information deletion, with attention to its desired availability, integrity, data quality and security.
The goal of a holistic approach to information governance is to make information assets available to those who need them, while streamlining management, reducing storage costs and ensuring compliance. This, in turn, helps the company reduce the legal risks associated with unmanaged or inconsistently managed information and become more agile in response to a changing marketplace.
An important goal of information governance is to provide employees with data they can trust and easily access for decision-making. In many organizations, responsibilities for data governance tasks are split among security, storage and database teams. Often, the need for a holistic approach to managing information doesn't become evident until a major event occurs, such as a lawsuit, compliance audit or corporate merger.
This article is part of
What is enterprise content management? Guide to ECM
Information governance provides a wide range of benefits. It ensures the following:
- Whoever requires access to certain information can receive it.
- Underlying data is properly managed, stored and secured.
- Regulatory requirements are correctly observed, where necessary.
- Risk management is in place to minimize any issues that might arise from incorrect use.
Why is information governance important?
Information governance makes information more accessible to those who need it, which is crucial for any organization. Organizations of all types and sizes often suffer from poor organization and management of information assets, leading to issues with accessibility, ease of use, timeliness and security -- all of which governance can positively affect.
Often, the same information exists in more than one location, leading to issues with updating and discrepancies that cause confusion. Effective information governance can establish a single source of truth, making information more trustworthy.
Effective information governance is so important that it has become a C-suite role in many organizations, with an executive responsible for its implementation. The chief information governance officer (CIGO) often oversees the initial governance initiative, shepherding its development, management and ongoing evolution throughout the organization. The CIGO is generally responsible for maintaining information integrity standards, gathering required quality and usage metrics and ensuring that the company meets compliance and regulatory requirements.
It's also increasingly common for enterprises to establish an information governance council composed of key stakeholders in the organization, including management-level representatives from every area of the business, IT personnel involved in infrastructure and security, and subject matter experts who fully understand how specific information is used. This governance council often helps the executive officer implement and enforce governance policy and can be invaluable in guiding its ongoing development.
A commitment to information integrity throughout the enterprise requires the active participation of employees at all levels and in all areas. Awareness of and commitment to information governance processes should be organization-wide, actively promoted and frequently updated.
What is the difference between data governance and information governance?
When considering information governance, it's common to wonder how it differs from data governance, which is referred to more commonly. The difference is subtle; data isn't necessarily information, whereas information can't exist without data.
Information governance refers to data assets that have carefully defined business meanings. Data governance, on the other hand, refers to the oversight of the physical data itself -- its storage, security and transport. Someone implementing data governance might perform those tasks with little or no understanding of the data's meaning, while, in information governance, meaning is everything.
Information governance challenges
Even a clear vision and strong management support don't guarantee information governance success. Organizations can experience the following common issues when implementing information governance:
- Compliance and regulatory issues. An organization often requires information governance during a lawsuit or some other consequence of noncompliance. On such occasions, compliance teams must go through potentially millions of pages of documents -- and possibly even more rows of data -- in pursuit of information that has been requested for legal purposes. This process, also called electronic discovery, is daunting even when things are orderly. It can become a nightmare if the organization's information isn't well-ordered and readily discoverable.
Organizations can mitigate this challenge using the following strategies: -
- Establishing a universal metadata taxonomy for consistent tagging of information.
- Developing a consistent retention management and defensible disposal policy and process.
- Establishing a classification program for sensitive data to rate all information assets for its sensitivity.
- Big data and machine learning. Machine learning is essential in the enterprise, as it enables the predictive and prescriptive analytics that are necessary to maintain a competitive edge. But machine learning depends on big data -- large amounts of information about the particular domain being modeled for predictive use -- and it's often challenging to manage data of that magnitude.
Careful attention to the integrity of data sources and the merging and transformation of data from multiple sources is essential in this endeavor. Organizations should ensure that the big data underlying the analytics is as accurate and clean as possible. A strong governance policy can help ensure this.
- Lifecycle management. A major challenge of any information governance implementation is the need to manage data that underlies information assets throughout its lifecycle in multiple domains. As silos come down and information becomes more centralized in the enterprise, inconsistencies in its management can creep into existing processes, causing friction between groups. All groups using common information must agree about the process of refreshing, modifying and archiving that information. Achieving information governance policies that encourage such agreement should be the responsibility of the governance officer and council.
Information governance frameworks
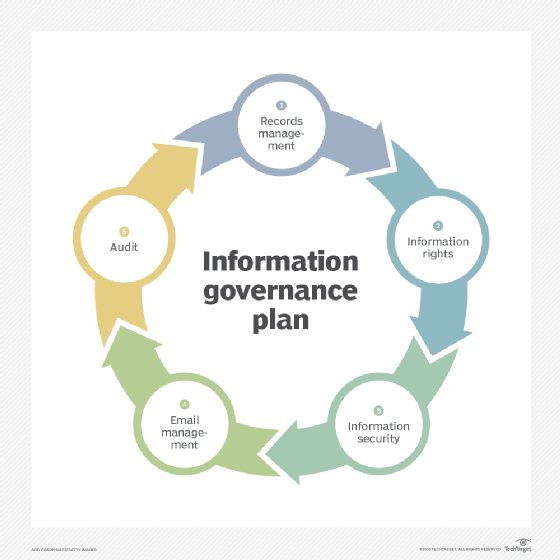
Different types of organizations have different goals and tasks, but the elements of information that are used to manage those activities are often similar. For this reason, it's possible to create frameworks to clarify an information governance plan that can be useful in organizing the effort, regardless of how customized the organization's handling of information seems.
These information governance plan frameworks outline the who, what, when, where, why and how of company information. Frameworks are built from the answers to some of the following central questions that apply to information of all types:
- What does this information mean?
- Who uses it?
- How is it created and where does it come from?
- What do users do with it?
- Who can access it?
- Why is it important?
- How long is it useful for?
- What other information depends upon this information?
Answering all these questions for every information asset within the enterprise is a monumental task. However, once an organization collects those answers, the path to managing those assets becomes increasingly clear.
Frameworks are tailored to the organization's unique governance needs but should define the following areas:
- Policy. The framework defines which wide-ranging, overall corporate policies and procedures are relevant to the information governance program, including the company's data security, records management, retention and disposal schedules, privacy and information sharing policies.
- Process. The framework carefully defines how information governance policies are implemented.
- Roles and accountability. Who does what is a key part of policy implementation and process. The accountability framework defines the information governance program's key roles, including what information governance responsibilities specific employees and departments will have as part of the program's implementation and integration. For example, who has ultimate responsibility for the management of specific bodies of information, particularly sensitive ones? What are the consequences of mismanagement in this area?
- Metrics. Organizations can track information quality, access and lifecycle management by measuring activity, quality of outcomes and issues. Strong metrics make for strong processes and effective risk management.
- Compliance. A framework highlights legal and regulatory concerns to ensure they're addressed and to specify how.
- Scope. The framework establishes the extent of the information governance program, including clearly outlining its overall goals, which staff members will be involved in achieving these goals and the types of data the information governance program is designed to manage.
- Internal and external data management. The information governance framework defines how employees and the organization manage specific data, with relevant sections including legal and regulatory compliance; acceptable content types; how personal information is managed; how information is stored, archived and disposed of; and how information is shared.
It's also essential to establish how the organization operates and shares information with stakeholders, partners and suppliers. The framework should define the policies and procedures for sharing information with third parties; how the information governance process influences contractual obligations; and how the organization determines whether third parties are meeting its information governance goals. - Disaster recovery (DR) and business continuity (BC). The framework should clearly outline company procedures in the event of a data breach, including how to report information losses and breaches, incident management specifics, DR processes, BC strategies, and auditing these DR and BC processes.
- Continuous monitoring. The framework should outline plans for quality assurance of information governance processes, including how the company will monitor information access and use, measure regulatory compliance adherence, maintain effective security, conduct risk assessments and periodically review the information governance program as a whole.
Laws, regulations and principles
Information governance isn't just a matter of best practices; it's a matter of regulation in and of itself because it's so deeply intertwined with security, privacy and compliance concerns.
As technological innovations continue to expand business capabilities and corporate data volumes grow, regulations that put strict mandates on information governance processes have become the norm. This is especially true for data privacy and security, as personally identifiable information has become a target for hackers and nefarious online actors. Privacy laws, such as the European Union's Data Protection Directive, have started to expand in countries all over the world and create new information security governance obligations for companies.
Many industries, including highly regulated sectors, such as energy and financial services, require records and electronic communications to be retained for a minimum period. These regulations include mandates from federal agencies, such as the Securities and Exchange Commission, Department of Justice and Environmental Protection Agency, regarding response times for information requests. Regulatory reporting requirements also often mandate that companies provide an account of compliance, usually in the form of raw or summary data, with set frequency, such as annually.
Examples of laws and regulations that information governance can address include the following:
- The Health Insurance Portability and Accountability Act (HIPPA). HIPAA is a good example of regulatory requirements that can be addressed through effective information governance. HIPAA imposes strict compliance requirements on healthcare organizations to compel them to protect the privacy of patient medical information.
- The European Union's General Data Protection Regulation (GDPR). GDPR is a regulatory effort to preserve consumer privacy. It calls for organizations to empower customers to control the amount of private information that a company can share. This is another area where information governance is critical and empowering.
- The Foreign Corrupt Practices Act (FCPA). FCPA addresses compliance, imposing rules on organizations to ensure the authenticity of the records they keep. The idea is that organizations will be able, if called upon, to produce evidence of information authenticity -- yet another process for information governance.
Information governance models
In addition to frameworks, there are information governance models. Organizations can use these to assess the quality and effectiveness of an information governance program once they implement it.
- Information Governance Reference Model (IGRM). IGRM gives organizations a way to communicate the processes, policies and responsibilities of an information governance program with its key stakeholders. Its goal is to establish a clear mapping of information management responsibilities within the organization and among its partner organizations.
- Information Governance Maturity Model (IGMM). IGGM is focused on best practices. It's built on the Generally Accepted Recordkeeping Principles, encouraging the implementation of processes that aren't only compliant, but progressive, spurring the organization to greater efficiency, competitiveness and customer focus.
- Information Governance Implementation Model (IGIM). IGIM establishes a common understanding of governance principles and policies among stakeholders, reducing risk and enhancing cooperation and broad uptake of processes.
What is information governance software?
Automated tools are available to support information governance in the enterprise. These tools include process automation and workflows that simplify and fortify repetitive information governance tasks, while providing audit trails for compliance purposes.
Examples of vendors that offer information governance tools are listed below in unranked, alphabetical order:
- Alation.
- Collibra.
- Egnyte
- Erwin.
- IBM.
- Informatica.
- Qlik
- SAP.
- SAS.